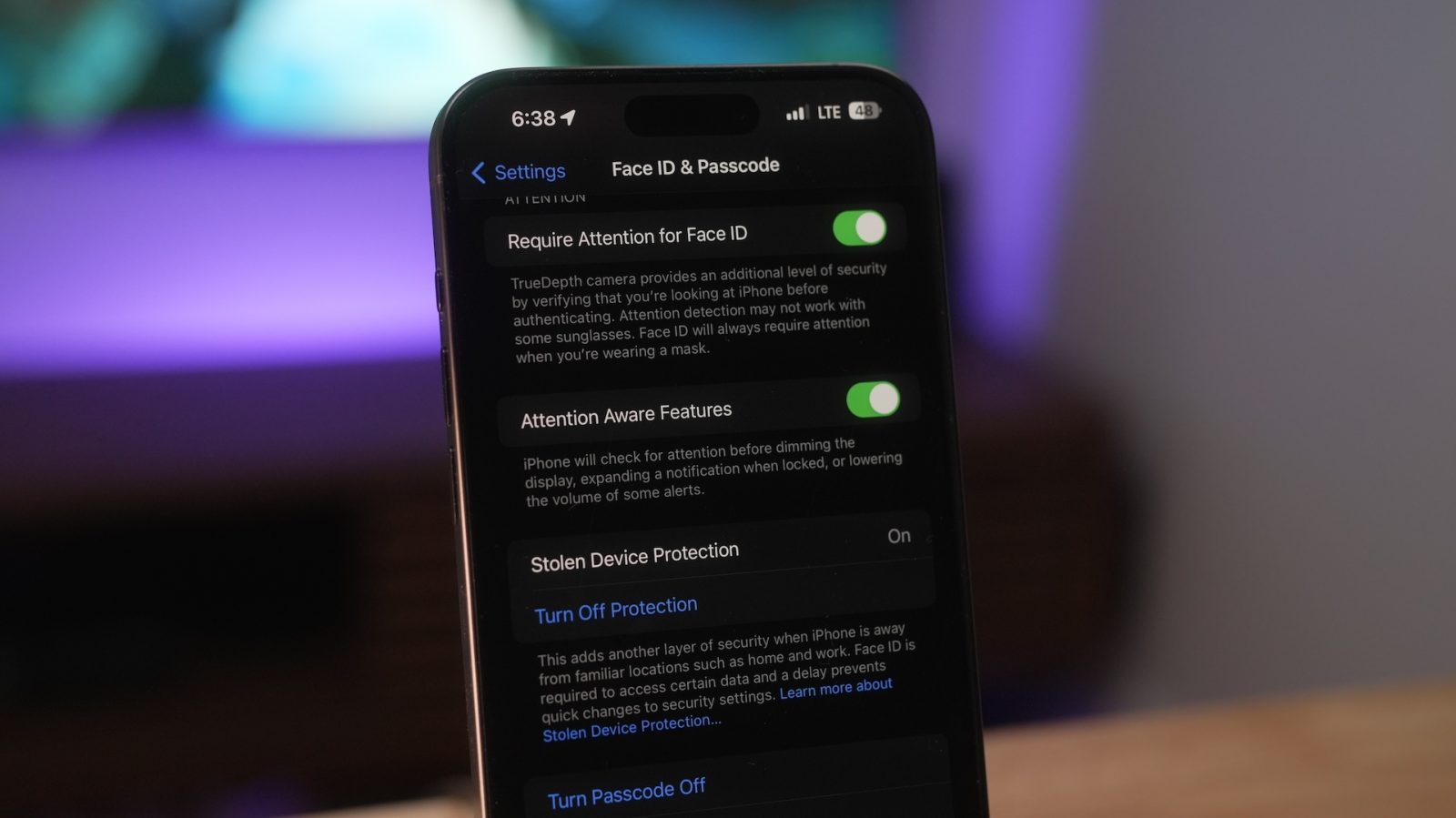
Last week, Apple released iOS 17.3 with a new security feature called Stolen Device Protection, which aims to help protect your data in case a thief has stolen your iPhone and obtained the password. However, one fatal flaw has already been discovered…
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.
This is Security Bite, your weekly security-focused column on 9to5Mac. Every Sunday, Arin Waichulis delivers insights on data privacy, uncovers vulnerabilities, and sheds light on emerging threats within Apple’s vast ecosystem of over 2 billion active devices. Stay secure, stay safe.

The Stolen Device Protection feature comes after the Wall Street Journal’s Joanna Stern investigated a rise in iPhone thieves in restaurants and bars, with one criminal making as much as $300,000. The attacks were typically carried out by observing victims entering their passcode before stealing the device, changing their Apple ID password, and turning off Find My iPhone to make it impossible to track or wipe remotely. From here, a thief can lock victims out of accounts (i.e., Venmo, CashApp, other banking apps, etc) by using passwords saved to the Keychain password manager.
Fortunately, Stolen Device Protection helps thwart this vulnerability in two key ways. When enabled, the feature requires Face ID or Touch ID authentication (with no passcode fallback) before users can change important security settings like Apple ID passwords or device passcodes. It also enacts a one-hour security delay before users can change these security settings. This is designed to give victims time to mark an iPhone as lost before a thief can make critical changes.
Fatal flaw in Stolen Device Protection
However, if a user has Significant Locations enabled and is currently located in a familiar location, they won’t get these extra layers of security.
“When your iPhone is in a familiar location, these additional steps are not required, and you can use your device passcode like usual,” states Apple in the Stolen Device Protection support documents. “Familiar locations typically include your home, work, and certain other locations where you regularly use your iPhone.”
Apple deems a location significant based on how often and when a user visits it. This data is typically used for things like Siri Suggestions and Memories in the Photos app, but as it’s also used for Stolen Device Protection, this can be concerning if you frequent a particular bar or cafe, notes popular technology YouTuber ThioJoe in a post on Twitter (X).
“By default, the protections are nullified when at a familiar location. The problem is you have NO CONTROL over what is familiar,” ThioJoe writes. “The most recent was even a place I had visited for only a few hours ONCE this past weekend..” Lots of clown emojis in the tweet, and rightfully so. Being unable to view and edit your familiar locations is a little bizarre for Apple, known for its user privacy and transparency.
The problem occurs if your iPhone marks your favorite bar, restaurant, or public hangout spot as “familiar.” Stolen Device Protection can be toggled off without the need for biometric authentication. ThioJoe was able to disable the feature at one of his familiar locations (home) without Face ID. In my testing, I was able to disable Stolen Device Protection from a coffee shop I admittedly work from almost daily by also failing Face ID authentication and using the passcode as a fallback.
It’s unclear how Apple determines a significant location as a familiar location for Stolen Device Protection. Fortunately, you can turn off Significant Locations by going to Settings > Privacy & Security > Location Services > System Services > Significant Locations. When disabled, it will require Face ID or Touch ID, with no option to bypass it with a passcode, even when at a familiar location.
Notably, in Thursday’s iOS 17.4 beta 1 release, Apple added the ability to always require a security delay when changing security settings. This means a user will always have to wait an hour before changing their Apple ID password and other security settings. This is currently only available for beta testers and is not enabled by default.
I’ll continue to test and update this post.
More
FTC: We use income earning auto affiliate links. More.










